SBOMs are becoming a procurement baseline
Software buyers increasingly expect a clear component inventory to manage supply chain risk and response time.
Quick Take
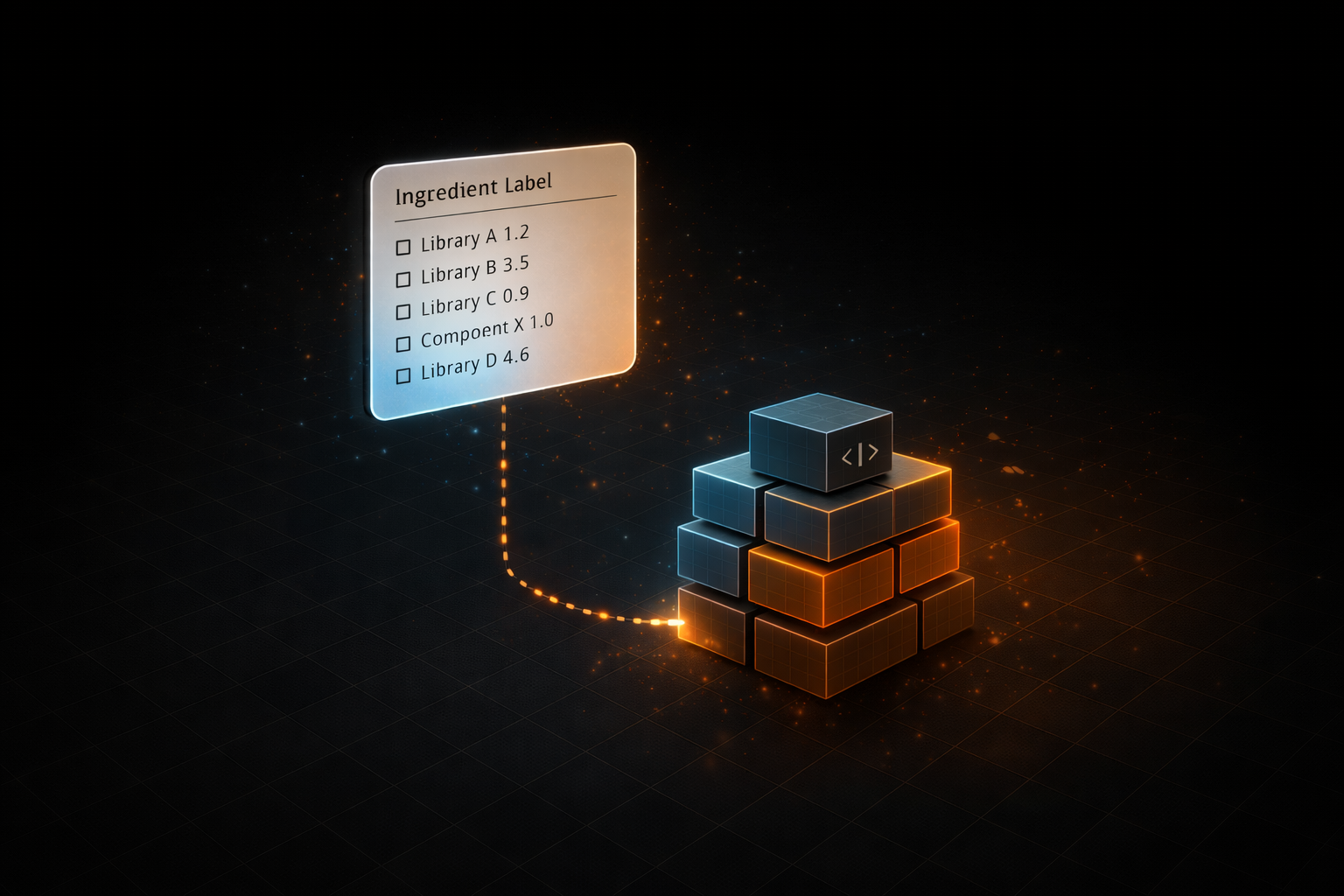
SBOM stands for Software Bill of Materials: an 'ingredient list' for software. It is becoming a common procurement and security expectation because it reduces guesswork during incidents and speeds up vulnerability response. SBOMs do not make software secure by themselves, but they make risk visible and easier to manage. (CISA)
Why this moved from "security talk" to mainstream buying
Modern software is assembled from third-party and open-source components. When a widely used component has a vulnerability, the first question is basic: are we affected, and where. An SBOM exists to answer that question quickly, without manual archaeology across repos and build artifacts. (NIST) Adoption is also being pulled by policy and institutional buyers. U.S. federal cybersecurity efforts elevated SBOMs as part of software supply chain transparency, and guidance has been formalized into "minimum elements" that are intended to be exchanged across organizations. (NIST)
What an SBOM is, and what it is not
An SBOM is a structured record of the components that make up a software product and their relationships, comparable to an ingredient label. It typically includes component names and versions in a machine-readable form so downstream organizations can automate inventory and response workflows. (NIST) An SBOM is not a security certificate, a guarantee of safety, or a substitute for secure development. It does not tell you that your system is safe. It tells you what is inside your system, which is the prerequisite for doing anything sane when risk appears.
Why procurement cares now
Procurement is a risk function, even when it pretends to be paperwork. For many buyers, an SBOM is becoming a baseline signal that a vendor can answer supply chain questions under pressure: what components are included, what is affected by a disclosed vulnerability, and how quickly the vendor can act. (CISA) This changes the vendor conversation from "trust us" to "show us the inventory." It also creates a shared language between security teams, legal/compliance, and engineering. When the record is structured and repeatable, it is easier to evaluate software at scale instead of handling every incident as a bespoke event.
What implementation looks like in practice
In real teams, "having an SBOM" usually means generating it automatically during builds, producing it per release, and keeping it current as dependencies change. The NTIA minimum-elements work exists specifically to prevent "everyone calls it an SBOM but nobody can exchange it," by setting expectations around baseline contents and use cases. (NTIA) The common failure mode is performative compliance: generating an SBOM once, then letting it drift, or generating one that is technically valid but operationally useless because nobody can map it to what is deployed. The value comes from lifecycle handling: build-time generation, release tracking, and the ability to answer "are we affected" quickly and consistently. (CISA)
Signal
What most teams underestimate is maintenance and operational linkage: an SBOM that is not continuously updated and tied to incident response becomes a document artifact, not a risk control. (CISA)